outlook安全模式修复
Microsoft is one of the biggest tech companies in the world, and yet their online email service, Outlook.com, does very little to protect its users from one of the most dangerous cyber crimes of modern digital life.
微软是世界上最大的科技公司之一,但其在线电子邮件服务Outlook.com并没有采取什么措施来保护其用户免受现代数字生活中最危险的网络犯罪之一的侵害 。
I have been using Outlook.com (A.K.A. Hotmail) for a longtime, and even though I switched my daily use to Gmail a decade ago I still maintain my account as a second option, having some old services still connected to it, just to avoid the hassle of moving them over to Gmail.
我已经使用Outlook.com(AKA Hotmail)很久了,即使十年前我将日常使用切换到Gmail,我仍然将帐户作为第二选择,仍然连接了一些旧服务,只是为了避免将它们转移到Gmail的麻烦。
Microsoft has put some effort to improve Outlook.com in recent years, but the security side of their email service apparently didn’t get the same level of attention as the shiny new features did.
近年来,Microsoft做出了一些努力来改进Outlook.com ,但是其电子邮件服务的安全性方面显然没有像闪亮的新功能那样受到关注。
This is an email I received recently in my Focused Inbox, Outlook’s machine learning solution to filter the most relevant and desired emails:
这是我最近在Outlook的机器学习解决方案“ 聚焦收件箱”中收到的电子邮件,用于过滤最相关和最需要的电子邮件:
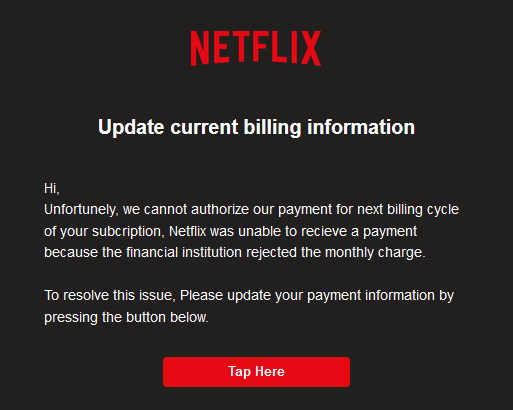
Seems legit, right? Especially since Outlook’s Artificial Intelligence so smartly decided to place it under my Focused Inbox, it must be really important for me to click on that big red button, I guess.
看起来合法,对吧? 我猜想,尤其是因为Outlook的人工智能如此明智地决定将其放置在“ 聚焦收件箱”下 ,所以对于我来说,单击那个红色大按钮对我来说确实非常重要。
The AI figured I would miss my beloved series if Netflix got cancelled for a payment issue, thus it pushed this email right into my Focused Inbox, which in turn even gives me an instant notification on my smartphone’s Outlook.com App, so I can click that beautiful red button even quicker.
AI认为,如果Netflix因付款问题而被取消,我会错过我心爱的系列,因此它将电子邮件直接发送到我的Focused Inbox中 ,这反过来甚至使我在智能手机的Outlook.com App上获得了即时通知,因此我可以单击那个漂亮的红色按钮更快。
And that’s where the problem lies: This is a Phishing attack!
这就是问题所在:这是网络钓鱼攻击!
Phishing is a type of cyber crime where criminals randomly send thousands of fake emails (bogus phone calls or text messages are also methods of Phishing), pretending to be a trustworthy party, in the hopes that someone, somewhere around the globe, will click on the email’s link or download an attached file (usually an executable containing malware), which then usually leads to stealing the victim’s personal data, credit card information, banking accounts and etc. which can result in identity theft and financial loss.
网络钓鱼是一种网络犯罪 ,犯罪分子随机发送数千个伪造的电子邮件(伪造的电话或短信也是网络钓鱼的方法),假装自己是一个值得信赖的政党,希望世界各地的某人点击电子邮件的链接或下载附件(通常是包含恶意软件的可执行文件),然后通常会导致窃取受害者的个人数据,信用卡信息,银行帐户等,这可能导致身份盗用和财务损失。
The victim’s data theft is usually done by opening a fake website after the victim clicks on a fake email link (in my case that red button), pretending to be some sort of real service (in my case Netflix), asking for personal information, like pretending there’s a problem with some payment or a password (in my case filling a billing form on the fake website with my credit card information). Once the victims add their true information, that can be further used to steal their money/data.
受害者的数据盗窃通常是通过在受害者单击伪造的电子邮件链接(在我的情况下为红色按钮),假装为某种真实服务(在我的情况下为Netflix)之后打开假网站来询问个人信息,例如假装某些付款或密码有问题(在我的情况下,是在假网站上用我的信用卡信息填写帐单)。 一旦受害者添加了他们的真实信息,这些信息就可以进一步用于窃取他们的金钱/数据。
There are many forms of Phishing, to name a few: Spear phishing, Whaling, Vishing, BEC, and others. BEC is a very important one, it stands for Business Email Compromise, it’s a technique where criminals gain access to a company’s (Government or NPO) email accounts, sending emails pretending to be someone at the company, like the CEO for example.
网络钓鱼有多种形式,仅举几例: 鱼叉式网络钓鱼 , Whaling , Vishing , BEC等。 BEC是非常重要的一个,它代表“ 企业电子邮件妥协” ,这是一种使罪犯能够访问公司(政府或NPO)电子邮件帐户的技术,可以发送伪装成该公司某人的电子邮件,例如CEO。
Usually, BEC fraudulent emails include: fake invoices to clients and partners, where the money goes instead to the criminal; fake authorization orders, asking subordinates to approve or send payments; asking for client confidential data, so it can be used to attack that client, or just to ask for a ransom for not releasing the data.
通常,BEC欺诈性电子邮件包括:发给客户和合作伙伴的虚假发票,而钱却转给了罪犯; 伪造的授权命令,要求下属批准或发送付款; 要求客户提供机密数据,因此可以将其用于攻击该客户,或仅索取赎金以免释放数据。
Phishing, particularly BEC, is very dangerous, especially for non-tech savvy people. According to the FBI’s Internet Crime Complaint Center (IC3), in 2019 alone 114,702 Americans were victims of Phishing, which translates to a total loss of $57,836,379.
网络钓鱼,特别是BEC,非常危险 , 特别是对于那些不懂技术的人 。 根据FBI的互联网犯罪投诉中心(IC3)的数据 ,仅在2019年,就有114,702名美国人成为网络钓鱼的受害者,这意味着总计损失了57,836,379美元。
If we look into BEC complaints, those are 23,775 victims, which might seem less, but remember, those are businesses, and they took a financial loss of over $1.77 Billion! If we look worldwide, between June 2016 and July 2019, BEC accounts for losses over $26 Billion!
如果我们调查BEC的投诉,那是23,775名受害者,这似乎少了一些,但请记住,这些都是企业,他们蒙受了超过17.7亿美元的财务损失! 如果放眼全球, 2016年6月至2019年7月 ,BEC造成的损失超过260亿美元!
BEC is especially dangerous in Outlook.com, since it’s advertised as the online email service for Microsoft Office 365 users, which are mostly businesses. Many of those probably with owners over 50 years old, not fully aware of modern digital life risks, and more prone to open the wrong email.
BEC在Outlook.com中尤其危险,因为它被宣传为Microsoft Office 365用户(主要是企业)的在线电子邮件服务。 其中许多人的所有者可能超过50岁,他们并不完全了解现代数字生活的风险,并且更容易打开错误的电子邮件。
Fortunately to me, I know how to identify those attacks, and guess what, it’s really easy! You don’t need an advanced AI to know how to separate phishing from regular email, let me show you how you do it:
对我来说幸运的是,我知道如何识别这些攻击,然后猜测是什么,这真的很容易! 您不需要高级的AI就能知道如何将网络钓鱼与常规电子邮件分开,让我向您展示如何做:
1.查看“ 发件人” (1. Look at the “Sender”)
Phishing emails usually won’t match the name of the service or it will be something close, pretending to be them, like “[email protected]”, where “netflix-business.com” isn’t the real Netflix domain, that would be “netflix.com”.
仿冒电子邮件通常与服务名称不匹配,否则将很接近,假装为此类电子邮件,例如“ [email protected]” ,其中“ netflix-business.com ” 不是真正的Netflix网域,那就是“ netflix.com ” 。
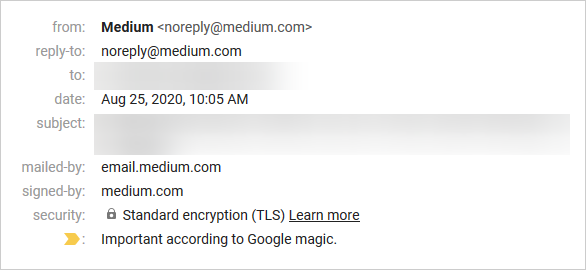
This is the sender of that email:
这是该电子邮件的发件人:

See? They didn’t even try to fake Netflix’s website address at all, and still, it went straight out to my Inbox. More so, this long gibberish is something any automated filtering system should easily detect with no effort.
看到? 他们甚至根本没有试图伪造Netflix的网站地址,但仍然直接进入我的收件箱。 更重要的是,这种漫长的胡言乱语是任何自动化过滤系统都应该轻松进行检测的。
Also trusted services will use secure email communication protocols (like TLS, DKIM, SPF and DMARC) for sending their emails, which won’t allow for the sender’s address to be tempered with (like if someone in the old days decided to fill another person’s name as the sender of a letter), so only Netflix will be able to write “netflix.com”. Gmail shows a nice padlock icon for encrypted messages, and a “signed-by:” field, where the sender address is verified (if you click to expand the message’s details), but I can’t find this information anywhere in Outlook.com, so one more problem right there.
另外,受信任的服务将使用安全的电子邮件通信协议(例如TLS , DKIM , SPF和DMARC )来发送电子邮件,这将使发送者的地址受到控制(例如,如果过去有人决定填充其他人的电子邮件,名称为信件的发件人),因此只有Netflix才能写出“ netflix.com ” 。 Gmail显示了一个用于加密邮件的漂亮的挂锁图标,以及一个“ 签名人:”字段,用于验证发件人地址(如果您单击以展开邮件的详细信息),但我无法在Outlook.com的任何位置找到此信息。 ,因此还有一个问题。
2.将光标放在链接或按钮的顶部 (2. Place your cursor on top of the link or button)
But DO NOT CLICK IT, and look at your browser’s bottom-left corner, the link’s destination address should appear there. Usually, this link would also try to resemble the original website’s address of the service, but normally, the criminals don’t even care. This is what I got:
但是请不要单击它 ,并查看浏览器的左下角,链接的目标地址应显示在此处。 通常,此链接还会尝试类似于该服务的原始网站地址,但通常情况下,犯罪分子甚至不在乎。 这就是我得到的:
Again, not even close to Netflix, but they tried to include the wording “payment-service” in there to camouflage things a bit.
再说一次,甚至与Netflix都不近,但他们试图在其中加入“支付服务”一词 ,以伪装一些东西。
Some phishing attacks can be quite elaborate, but as you can see this is a very simple one and still Outlook.com’s security filters failed miserably and delivered it straight to my main inbox.
某些网络钓鱼攻击可能非常复杂,但是您可以看到,这是一种非常简单的攻击,但Outlook.com的安全筛选器却惨遭失败,并直接将其传递到我的主收件箱中。
The worse part? I get emails like this on a weekly basis! How hard is it for Microsoft to keep this stuff out of my MAIN inbox? It’s not like this is a problem for their competition, I can’t even remember getting a single phishing email in Gmail.
更糟糕的部分? 我每周都会收到这样的电子邮件! 微软将这些东西排除在我的主收件箱之外有多难? 这并不是他们竞争的问题,我什至不记得在Gmail中收到一封网络钓鱼电子邮件。
The Outlook.com team is so aware that phishing is a plague in modern society that they built a dedicated button for it. This way we can classify an email as phishing so they could use this information to train their AI into better sorting phishing emails out of our inboxes:
Outlook.com团队非常清楚网络钓鱼在现代社会中是一个困扰,他们为此专门建立了一个按钮。 这样,我们就可以将电子邮件分类为网络钓鱼,以便他们可以使用此信息来训练自己的AI,使其更好地将收件箱中的网络钓鱼电子邮件分类为:
Does it work you ask? No, not at all. I always mark each single phishing email I get and I still keep receiving them. These emails I got just this month:
你问它有用吗? 一点都不。 我总是标记收到的每个网络钓鱼电子邮件,但仍会继续收到它们。 我本月刚收到的这些电子邮件:
Microsoft has a very talented team of cybersecurity professionals, it also invests heavily into AI, and promotes Outlook.com into their very successful and lucrative Office suite. I honestly can’t understand why their phishing detection algorithms didn’t evolve like the rest of their email service or their competitors.
微软拥有一支非常有才华的网络安全专业人员团队 ,它还对AI进行了大量投资 ,并将Outlook.com推广到他们非常成功且利润丰厚的Office套件中。 老实说,我不明白为什么他们的网络钓鱼检测算法没有像其他电子邮件服务或竞争对手那样发展。
Some might think phishing isn’t a security flaw, but I disagree. The whole point of a security solution is to keep its users safe, no matter the threat they are exposed to. If an Antivirus fails to detect malware, I call it flawed. If your business hire a security officer that fails to identify a robbery, I call your security flawed. Phishing filters are supposed to keep us safe, if they fail, well, I think it reasonable to call it a security flaw.
有些人可能认为网络钓鱼不是安全缺陷,但我不同意。 安全解决方案的重点在于确保用户安全,无论用户受到什么威胁。 如果防病毒软件无法检测到恶意软件,我称之为有缺陷。 如果您的企业雇用了无法识别抢劫案的安全人员,那么我称您的安全存在缺陷。 仿冒网站筛选器应该能够保护我们的安全,如果它们失败了,我认为将其称为安全缺陷是合理的。
I also want to point out that this article is based on my personal experience with both Outlook.com and Gmail. I couldn’t find any statistical data comparing the rate of phishing on both platforms, but I still feel confident on calling Outlook.com’s protection flawed, as the phishing emails I get are supposed to be very easily identifiable by any modern anti-spam/phishing filter:
我还想指出,这篇文章是基于我对Outlook.com和Gmail的个人经验。 我找不到比较这两个平台上网络钓鱼率的任何统计数据,但我仍然对将Outlook.com的保护称为缺陷感到充满信心,因为我收到的网络钓鱼电子邮件应该很容易被任何现代的反垃圾邮件/网络钓鱼过滤器:
- They come with famous services names (Netflix, PayPal). 它们带有著名的服务名称(Netflix,PayPal)。
- The sender email address doesn’t match any of the service’s known addresses. 发件人的电子邮件地址与服务的任何已知地址都不匹配。
- The sender email address is full of long gibberish. 发件人的电子邮件地址中有很多乱码。
- The email includes text relating to payments and financial transactions. 该电子邮件包括与付款和财务交易有关的文本。
My hope with this article is to promote awareness into this problem, so if you use Outlook.com please be aware of every email you get. If you know someone that might be prone to fall for this kind of scam, or if you work at Microsoft, or know someone that does, please forward this article to the right people, so this security issue can be mitigated, with fewer people having to risk their life savings being drained from their bank accounts, just by accidentally clicking the wrong button on their trusted email service.
我希望本文能够提高人们对该问题的认识,因此,如果您使用Outlook.com,请注意收到的每一封电子邮件。 如果您知道某个人可能会因这种骗局而堕落,或者如果您在Microsoft工作,或者知道会这样做的人,请将本文转发给合适的人,这样就可以减轻安全问题,而只有很少的人仅通过不小心单击其受信任的电子邮件服务上的错误按钮,就可能会冒着积蓄从银行帐户中耗尽的风险。
outlook安全模式修复